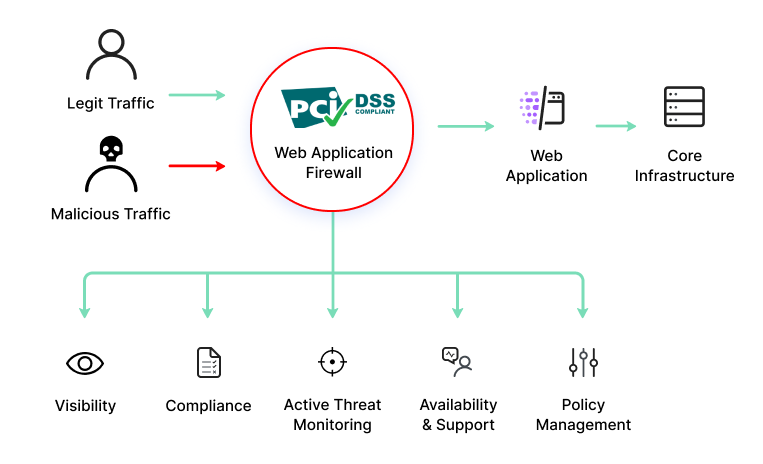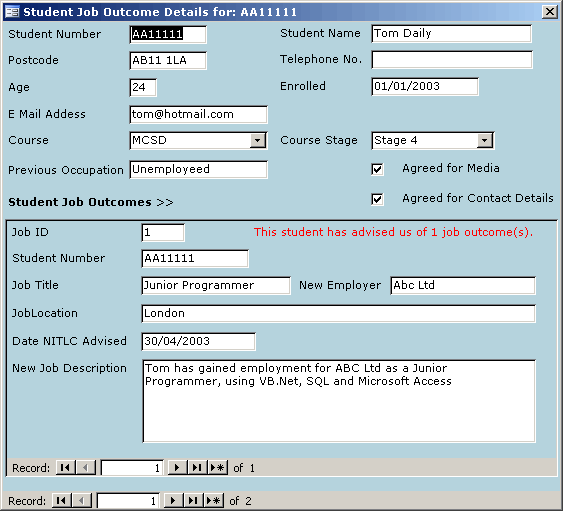
Prevent Duplicate Information from being entered into a Microsoft Access form | Database Solutions for Microsoft Access | databasedev.co.uk
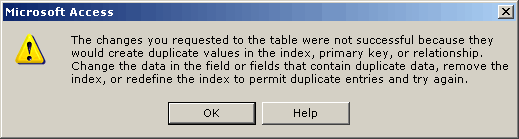
Prevent Duplicate Information from being entered into a Microsoft Access form | Database Solutions for Microsoft Access | databasedev.co.uk
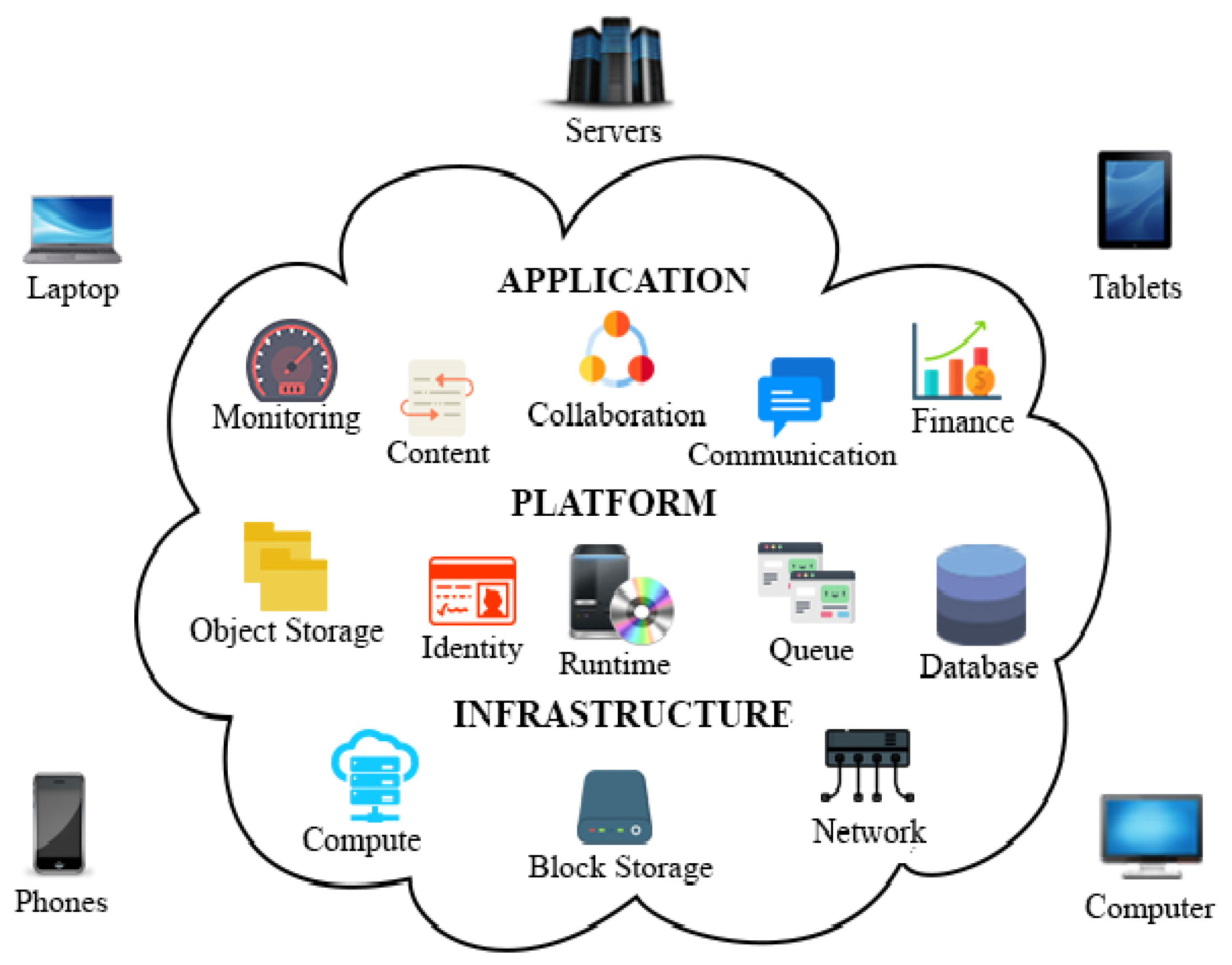
Electronics | Free Full-Text | A Survey on Modern Cloud Computing Security over Smart City Networks: Threats, Vulnerabilities, Consequences, Countermeasures, and Challenges
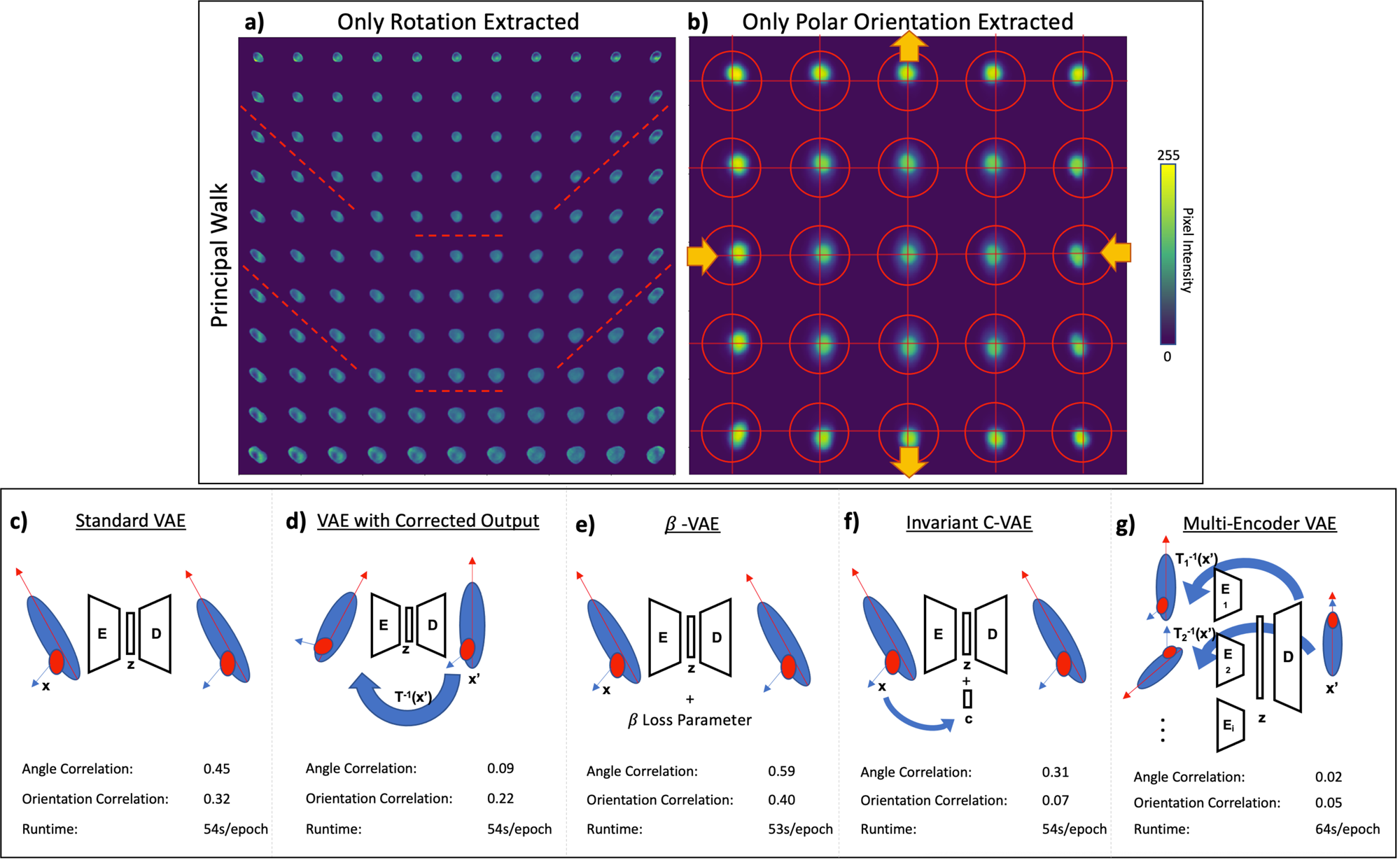
A multi-encoder variational autoencoder controls multiple transformational features in single-cell image analysis | Communications Biology





![Fix Access Denied Errors with Ease [CMD, Hard Drive, Folder] Fix Access Denied Errors with Ease [CMD, Hard Drive, Folder]](https://cdn.windowsreport.com/wp-content/uploads/2021/11/Access-is-denied-Windows-10-1200x900.jpg)